MISSION12 goo.gl/kBeZex(in polish) DIFFICULTY: ██████░░░░ [6/10]
┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅
While searching through captured drives, we've found an encrypted ZIP file.
Since we don't know the password - and have reasons to suspect it's strong,
thus not guessable nor breakable - we're turning to you, requesting your help.
goo.gl/zYoYiq
Good luck!This time the write-up will be a little bit different, as the way I solved it is… pretty damn boring. I’ve literally spent fair amount of time just reading specifics of what ZIP file, and its format is. That being said, let’s see what got on our tinkering station this time.
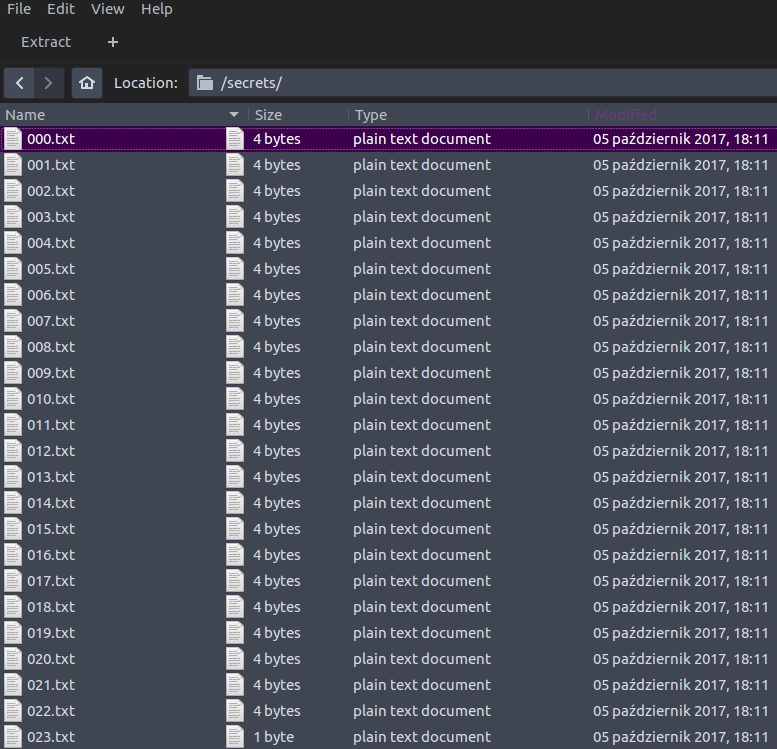 Okay, so bunch of txt files, weirdly even in their size.
Okay, so bunch of txt files, weirdly even in their size.
So… after reading about ZIP, we eventually learn it uses CRC32. Delving into what CRC is, we find out it’s reversible, if the initial (in our case) string is exactly 4 (or less than 4) bytes long. How peculiar, coincidentally all the files, except one, in our ZIP are 4 bytes big.
Well, that being said, let’s see if we can guess the content of our encrypted files. First, let’s retrieve the content CRCs.
fox@fox-desktop:~/Downloads$ zipinfo -v secrets.zip | grep CRC
32-bit CRC value (hex): 00000000
32-bit CRC value (hex): 7a5a8805
32-bit CRC value (hex): 42661db3
32-bit CRC value (hex): 0697339d
32-bit CRC value (hex): d27eea40
32-bit CRC value (hex): 79e36fca
32-bit CRC value (hex): 4b1587fd
32-bit CRC value (hex): a65fa2d1
32-bit CRC value (hex): 339f6b3c
32-bit CRC value (hex): 04cc23db
32-bit CRC value (hex): ede6bb0f
32-bit CRC value (hex): e3039df9
32-bit CRC value (hex): b64d1cb7
32-bit CRC value (hex): b961c051
32-bit CRC value (hex): b7829373
32-bit CRC value (hex): 5ae5c062
32-bit CRC value (hex): 1dde116c
32-bit CRC value (hex): ed5af2eb
32-bit CRC value (hex): 3f1ad5da
32-bit CRC value (hex): 3b14214c
32-bit CRC value (hex): b66f8037
32-bit CRC value (hex): 8ebd47de
32-bit CRC value (hex): 50810704
32-bit CRC value (hex): 0e201f1c
32-bit CRC value (hex): 9e6bffd3Great, we can drop the 00000000 as it’s just the folder our files are stored in. Now to guess what the strings resulting in these CRCs are!
from zlib import crc32
from itertools import product
from string import printable
zipcrc = [int(x, 16) for x in [ "7a5a8805", "42661db3", "0697339d", "d27eea40", "79e36fca",
"4b1587fd", "a65fa2d1", "339f6b3c", "04cc23db", "ede6bb0f",
"e3039df9", "b64d1cb7", "b961c051", "b7829373", "5ae5c062",
"1dde116c", "ed5af2eb", "3f1ad5da", "3b14214c", "b66f8037",
"8ebd47de", "50810704", "0e201f1c", "9e6bffd3" ]]
for char in printable:
fcrc = crc32(char.encode()) & 0xffffffff
if fcrc in zipcrc:
print("secret %d => %s %d" % (zipcrc.index(fcrc), char, fcrc))
for data in product(printable, repeat=4):
dat = ''.join(data)
fcrc = crc32(dat.encode()) & 0xffffffff
if fcrc in zipcrc:
print("secret %d => %s %d" % (zipcrc.index(fcrc), dat, fcrc))which gives us a nice output of
fox@fox-desktop:~/Downloads$ python crc.py
secret 23 => ! 2657877971
secret 6 => away 2791285457
secret 20 => d yo 2394769374
secret 14 => for 1525006434
secret 3 => have 3531532864
secret 8 => h it 80487387
secret 17 => ling 1058723290
secret 16 => medd 3982160619
secret 13 => n't 3078787955
secret 19 => s an 3060760631
secret 5 => ten 1259702269
secret 2 => uld 110572445
secret 21 => ur C 1350633220
secret 12 => were 3110191185
secret 15 => you 501092716
secret 0 => And 2052753413
secret 1 => I wo 1113988531
secret 22 => RC32 236986140
secret 10 => , if 3808665081
secret 4 => got 2044948426
secret 11 => it 3058506935
secret 18 => kid 991174988
secret 9 => too 3991321359
secret 7 => wit 866085692Since I am lazy, let’s make it a little bit easier to read.
fox@fox-desktop:~/Downloads$ cat res.txt | sort --version-sort
secret 0 => And 2052753413
secret 1 => I wo 1113988531
secret 2 => uld 110572445
secret 3 => have 3531532864
secret 4 => got 2044948426
secret 5 => ten 1259702269
secret 6 => away 2791285457
secret 7 => wit 866085692
secret 8 => h it 80487387
secret 9 => too 3991321359
secret 10 => , if 3808665081
secret 11 => it 3058506935
secret 12 => were 3110191185
secret 13 => n't 3078787955
secret 14 => for 1525006434
secret 15 => you 501092716
secret 16 => medd 3982160619
secret 17 => ling 1058723290
secret 18 => kid 991174988
secret 19 => s an 3060760631
secret 20 => d yo 2394769374
secret 21 => ur C 1350633220
secret 22 => RC32 236986140
secret 23 => ! 2657877971Well, there we go. Our flag is “And I would have gotten away with it too, if it weren’t for you meddling kids and your CRC32!”. No explosions, no fireworks, not even firecrackers this time. Rather just somewhat boring task of learning more about ZIP. (Though at first I attempted brute-forcing the password, just in case the mission author wanted to fool us ;)