MISSION 016 goo.gl/zqvPQD DIFFICULTY: ████████░░ [8╱10]
┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅
Operation codename Pasokon
During the operational game our spy (codename Martin) managed to intercept
hostile communication.
goo.gl/MoYBAx
Unfortunately, we have no idea how to decode it. To make matters worse, our most
well versed in crypto agent (codename Scottie) is on a mission right now and
cannot help us. Your handler advised to use your skills.
The fate of the Chunar rests in your hands!
And remember - if something is not clear, you have a license to bruteforce.
Good luck!
Over and out.Martin and Scottie look suspicious, which somewhat suggests they might be relevant later.
Well, let’s take a look at what we got thrown at us this time.
UklGRmQRNgBXQVZFZm10IBAAAAABAAEAgLsAAAB3AQACABAAZGF0YUARNgAAAIEfEz3iVllrNXma
fyZ+73SFZOtNhjIGFEr0RtXkuOGguY6KgwOAXYRTkCejs7tz2KH3UxeWNY1Qj2ZBdqx+TH8WeHxp
ZVQcOj8cp/xC3QHAr6bdksKFLYB2gnmMl53EtJLQS+8LD98t30lUYcxyM33mf7p6AW6CWnJBWiQG
BWTlZMffrHmXgYjkgBmBHYlzmCeu5sgI57IG9SXhQq9b2W4xe/R/2HwMcjxgf0hNLGENo+0Fz2uz
h5zCiyWCR4BEhsCT5Kd1weDeVP7hHZk7plVtaqh4dn9sfpp1jGU+Tw80rRX29dzWSroCooOP8YMA
gPGDg48Cokq63Nb29a0VDzQ+T4xlmnVsfnZ/qHhtaqZVmTvhHVT+4N51weSnwJNEhkeAJYLCi4ec
.
.
.
S8pUr1WZqolLgbuABIixlt2rOMYj5MUDLCNoQKxZaW1netp/a31Cc/1hrkrFLvoPM/Bl0Xe1IJ7S
jJ6CJICMhYCSNKZxv6jcDvyxG585AVQ1ae13QH+7fmd2xmbQUN41mhfj96vY37tHo2WQZYQEgIaD
tI7eoOW4TtVZ9BsUoTIHTp9kAnUwfpZ/Hnkwa6ZWxTwkH5r/FeCHwsSoYZSghluA84FRi+GbnLI=…a huge pile of unintelligible gibberish. One that turns out to be base64 encoded something. (thanks to my dear friend, Awoo, base64 spidey sense for spotting that “=” at the end)
Let’s try decoding this monster, shall we? Luckily there are sites like this, which do the job just right.
Upon decoding, we receive .wav file, which sounds as if aliens were trying to communicate.
Opening the file in audacity and removing some unnecessary noise shows us something like this.
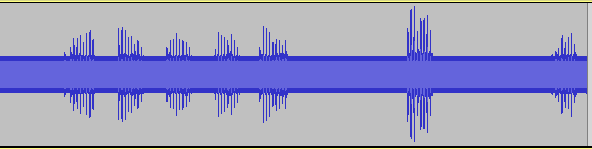 irregularities hint us it’s likely not binary nor morse (or alike) code
irregularities hint us it’s likely not binary nor morse (or alike) code
Dealing with similar messages in past, perhaps it’s a message hidden in spectrogram (which is fairly common in CTF tasks)?
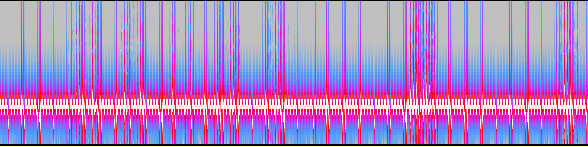 welp, it’s not
welp, it’s not
Perhaps that’s where Martin and Scottie should kick in. Maybe the message is encoded with their name as key?
fox@fox-desktop:~/Downloads$ steghide extract -sf decoded.wav
Enter passphrase:
steghide: could not extract any data with that passphrase!
fox@fox-desktop:~/Downloads$ steghide extract -sf decoded.wav
Enter passphrase:
steghide: could not extract any data with that passphrase!Also, what is this talk about bruteforce, perhaps we should try this approach just now?
Using this little tool and this dictionary, let’s start our mindless attempt at finding the holy grail. Doing anything is better than nothing, right?
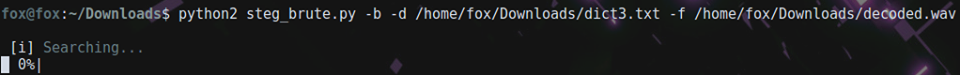 this will take some time… after 1-2 hours it only checked ~15% of the dictionary
this will take some time… after 1-2 hours it only checked ~15% of the dictionary
So… what is it then? After staring at the file in hexeditor and audacity, I noticed lot of similar, somewhat periodic, yet slightly different patterns, like this.
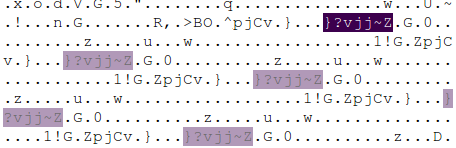 what the hell am I even trying to find
what the hell am I even trying to find
Is the message hidden in similar chunks, that only slightly differ to make the task harder? Am I even still sane? Trying to figure something out from periodic hex regularities for few hours led me nowhere.
Turns out I, indeed, do lack some common sense at times… thanks to TheAifam5 (hope I got the nick right!) suggestion of googling keywords like Martin Scottie which lead us to SSTV. Bingo.
I finally got, very needed, sanity check. He also managed to (better than I) decode the .wav.
 TheAifam5 attempt on the left, mine on the right
TheAifam5 attempt on the left, mine on the right
This is obviously some kind of cipher and not a flag we’re looking for, yet. What kind of cipher, though?
Well… now that we’re armed with common sense and Google let’s try looking for two other keywords, namely “Pasokon” and “Chunar”.
Looking for “Pasokon” led to this pdf, but we already got that.
What about Chunar then?
 well, it’s unlikely that’s the thing we’re looking for
well, it’s unlikely that’s the thing we’re looking for
It’s a cipher after all… so what about Chunar cipher? Ha, we’re finally onto something! Turns out Lord Playfair, born in Chunar, was reponsible for promoting cipher system invented by Charles Wheatstone, now known as Playfair cipher. Taking a look at what Playfair cipher is, we can be fairly certain the image we’ve decoded is ciphered this way.
??RON
DIYMA
UZ???
BCKP?
??VWX
Y DHXDMW BQLF KDYNVInitial thoughts: since letters in 5x5 matrix have to be unique, we can safely assume the 5th letter of 4th row is Q, as O is already present. After some more research, turns out I and J are treated the same in Playfair. This rules out J from the missing letters. The central letter kinda looks like L to me, so… let’s go with that. So.. what letters are left to be placed out there? “EFGHST”. “Y DHXDMW BQLF KDYN” is obviously ciphertext. Since the flag is most likely an English sentence, chances are Y, in reality, is I.
??RON
DIYMA
UZL??
BCKPQ
??VWX
Y DHXDMW BQLF KDYNVThis leaves us with 6! ways to place the missing letters, which isn’t too bad. Let’s try our luck with manual placing first.
After trying out various pairs and finding configurations of letters that made most sense to me, this is the furthest I’ve come.
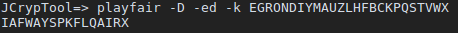 I way fair?
I way fair?
something doesn’t seem right… this is where Awoo, taking similar approach, being bit more sane person than I am, comes in. Turns out my (stupid) assumption of the central letter being L wasn’t quite correct. In fact… it was F.
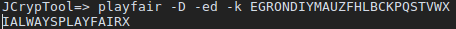 There is is. Our quest to find holy grail is completed. Turns out it was a mere chalice.
There is is. Our quest to find holy grail is completed. Turns out it was a mere chalice.
Thanks to both my friend Awoo and TheAifam5 whose hints pushed me to get closer to the solution. Notes to future self, and whoever might read it:
- Try not to fall into tunnel vision.
- Sanity check. Often.
- Read the damn mission at least a few times. I’ve googled a lot about how messages could be hidden within sound files, but didn’t think of looking for keywords in the mission description.